Technology
-

Serhiy Tokarev about Bridging the Gender Gap in Science and Technology
The issue of gender equality in science and technology remains relevant, despite the efforts being made. Women still make up…
Read More » -

The Cost of Reliability: Understanding UPS Inverter Price Points for Home and Office
UPS inverters are essential devices that ensure a continuous and stable power supply in both home and office settings. It…
Read More » -

Del Mar Energy: Revolutionizing Oil and Gas Extraction with BAGGETT 1-8D
Del Mar Energy, a pioneering American industrial holding, has once again pushed the boundaries of innovation with the completion of…
Read More » -

Mastering Web Application Development: A Guide to Experienced Specialists
Introduction In today’s digital age, web applications, serving as the backbone for various online services and platforms, have become an…
Read More » -

How to Recover Deleted Files Not in Recycle Bin
Problem finding deleted files not in the trash? Don’t worry. We have you covered. In the following section you’ll find…
Read More » -

Free Windows File Recovery Software – MyRecover
Since computer has become a important tool for you, data security on computers can be a significant factor for both…
Read More » -

iPhone Backup Software – FoneTool Reviews [Free Download]
Look for safe and professional iPhone backup software to back up your data? Some iPhone users (just like me) used to…
Read More » -
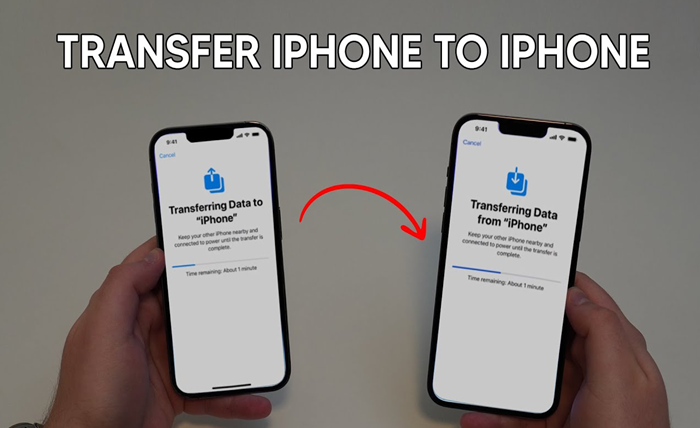
Easily Transfer iPhone to New iPhone Without Data Loss
Why do you want to move data from the old iPhone to a new iPhone? It can be prompted by…
Read More » -

How to Boost Your Snapchat Privacy Settings
It makes sense if you’re concerned that Snapchat could send you unexpected snaps and give up too much useful information.…
Read More » -

Maintaining Peace of Mind with Your Tech: Strategies for Security, Protection, and Recovery
Technology is integral to everyone’s lives, from managing finances and communication to entertainment and work. However, with the convenience and…
Read More »
